24.0.1.157

The IP address ‘24.0.1.157’ is an IPv4 address with specific implications for internet connectivity and security. Its geographical allocation can affect user anonymity and online interactions. Additionally, this address can serve as a critical tool in network troubleshooting, revealing connections and potential vulnerabilities. Understanding its characteristics and origins may uncover insights into broader cybersecurity practices. What remains to be explored are the nuances of its operational impact and the measures necessary for enhanced protection.
Understanding IP Addresses
IP addresses serve as the fundamental identifiers for devices within a network, enabling seamless communication across the internet.
Understanding IP categorization is essential, as it encompasses various address types, including IPv4 and IPv6. Each type serves a distinct purpose, facilitating efficient routing and connectivity.
Proper categorization promotes a decentralized and liberated internet, ensuring users maintain autonomy while navigating the digital landscape.
The Significance of ‘24.0.1.157’
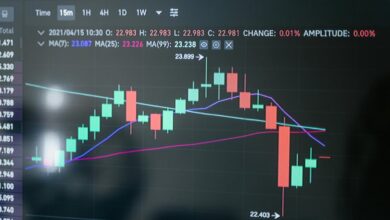
The IP address ‘24.0.1.157’ represents a specific point within the vast landscape of internet connectivity, classified under the IPv4 protocol. Its significance lies in its potential IP location, affecting data privacy and user anonymity.
| Aspect | Description | Importance |
|---|---|---|
| IP Location | Geographical position | Influences targeting |
| Data Privacy | User information security | Protects identity |
| Connectivity | Network accessibility | Enhances browsing |
Potential Origins of ‘24.0.1.157’
Understanding the origins of ‘24.0.1.157’ involves examining its allocation and the entities responsible for its assignment.
This IP address could potentially stem from various sources, which may include:
- Regional Internet Registries (RIRs)
- Internet Service Providers (ISPs)
- Specific geographical locations tied to user demographics
Each factor contributes to understanding its broader implications in network architecture and data routing.
Role in Network Troubleshooting
The IP address 24.0.1.157 plays a crucial role in identifying network issues by providing a reference point for troubleshooting connectivity problems.
By analyzing traffic patterns associated with this address, network administrators can pinpoint anomalies and determine the root causes of disruptions.
This systematic approach enhances the efficiency of network diagnostics and resolution processes.
Identifying Network Issues
How can one effectively identify network issues to facilitate efficient troubleshooting?
Employing robust network diagnostics and conducting thorough connectivity analysis are essential.
Key strategies include:
- Utilizing ping tests to check device reachability.
- Implementing traceroute to pinpoint latency sources.
- Analyzing logs for error patterns.
These techniques provide a structured approach, enabling swift identification of underlying network problems and facilitating timely resolutions.
Analyzing Traffic Patterns
Traffic analysis serves as a critical element in network troubleshooting, providing insights into data flow and identifying anomalies that may indicate underlying issues.
Through effective data visualization, network administrators can discern patterns and trends, enabling them to pinpoint sources of congestion, unauthorized access, or performance degradation.
This analytical approach fosters a more robust and efficient network environment, empowering users with greater operational freedom.
Implications for Cybersecurity
The vulnerabilities associated with addressing in network configurations present significant challenges for cybersecurity.
Effective mitigation strategies must be developed to address these weaknesses, as failure to do so may lead to increased susceptibility to cyber threats.
Additionally, organizations face regulatory compliance challenges that further complicate the implementation of robust cybersecurity measures.
Vulnerabilities in Addressing
Although addressing is a fundamental aspect of network architecture, vulnerabilities inherent in its implementation pose significant risks to cybersecurity.
Key concerns include:
- Inadequate vulnerability assessment practices leading to unrecognized threats.
- Misconfigured addressing schemes that expose sensitive data.
- Lack of addressing security measures, which facilitate unauthorized access.
These factors collectively undermine the integrity and confidentiality of network communications, necessitating a thorough examination of addressing vulnerabilities.
Mitigation Strategies Required
Addressing vulnerabilities necessitate robust mitigation strategies to enhance cybersecurity measures.
Effective network security must incorporate advanced traffic analysis techniques to monitor and respond to potential threats.
Implementing these strategies not only fortifies defenses but also empowers organizations to maintain operational integrity.
Regulatory Compliance Challenges
How can organizations navigate the complex landscape of regulatory compliance while ensuring robust cybersecurity?
- Understand relevant regulatory frameworks to align cybersecurity strategies effectively.
- Conduct regular compliance audits to assess adherence and identify vulnerabilities.
- Implement adaptive security measures that evolve with changing regulations.
Addressing these challenges requires a proactive approach to harmonizing compliance with cybersecurity objectives, thereby safeguarding organizational integrity and promoting a culture of accountability.
How to Gather Information From an IP Address
Gathering information from an IP address can provide critical insights into the origin and nature of network traffic. Techniques such as IP tracking and geo location are essential for this process. The following table outlines key aspects of information gathering from an IP address:
| Aspect | Description |
|---|---|
| IP Tracking | Monitoring the activity of a device using its IP address. |
| Geo Location | Identifying the physical location associated with an IP address. |
Conclusion
In the vast digital ocean, the IP address ‘24.0.1.157’ serves as a lighthouse, guiding data packets through the tumultuous waters of the internet. Its significance extends beyond mere connectivity; it embodies the intersection of user identity, security, and network integrity. By illuminating potential vulnerabilities and facilitating troubleshooting, this address symbolizes the delicate balance between accessibility and protection in the online realm. Understanding its nuances is essential for navigating the complexities of modern cybersecurity landscapes.